The reason why it will become so critical is that Threat Management allows us for the first time to build upon a complex conceptual framework with a variety of analytical tools which will automate an ever-growing percentage of Cyber Security tasks. Without this framework it would remain difficult or nearly impossible to manage Cyber Security in a proactive and coordinated manner. For the purposes of this discussion let’s define Threat Management as:
“The conceptual and technical framework dedicated to discovering, defining and managing threats to operational security and mission assurance. Threat Management is software & hardware agnostic and can apply as an integrated IT practice in any functional domain. The goal of Threat Management is not merely to ensure that immediate (local domain) threats are mitigated but that threats are also managed in the context of communities of interdependent or inter-related entities. Threat Management depends upon top-down, bottom-up and lateral participation or guidance to build knowledge frameworks which can then be used to define security policy and solution mitigation.”So, what is a “Threat” given this construct? A Threat is “any event, vulnerability or behavior (or combination thereof) that either poses a danger to the operational mission or if combined with other events, vulnerabilities or behavior could constitute a threat to the operational mission.”
 |
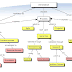
| The first step towards identifying threats is to define what threats actually represent |
In that last sentence we begin to see the systems implications of what we’re talking about. The goals here are two-fold; one – block a threat before it is manifested or two – stop a threat in motion that wasn’t blocked in time to preserve operational capability. The other key consideration here is that we’re viewing this practice as evolutionary – it learns as it goes and learns from the community which uses it.
Threat Management and Semantic Technology
Much of what we’re describing with Threat Management already occurs in some fashion; however that is not consistent from one enterprise to another and in fact much of it is handled using manual processes with little ability to correlate or manage various aspects of the problem in a unified approach. To unify Threat Management we need a mechanism which allows us to characterize all aspects of Threats and to correlate that information from information collected from the full spectrum of security related software or hardware appliances.
Threat Management as we’re describing it here is wholly dependent on a Semantic Knowledge layer and data exchange architecture. This allows us to:
- Provide non-proprietary data exchange approaches (for security-related data capture and analysis).
- Characterize complex or aggregated data “patterns” in utilizing ontologies or RDF-based databases or related tools.
- Provide a knowledge sharing framework for the community of defenders and security experts who analyze existing or predict future threats.
- Build policies based upon Threat Activity and Threat Prediction – policies that can also be captured, manifested and distributed using Semantic technology.
- Drive dynamic reconfiguration of H/W and S/W infrastructure in response to policy definition and distribution.
Copyright 2012, Semantech Inc. All Rights Reserved













0 comments:
Post a Comment