Several years ago, I was involved in an effort to build a Cyber Security Consortium. This initiative was focused primarily on the Federal marketplace but was not in any way limited to government-related missions or solutions. Our effort was one of several that sprang up more or less at about the same time - most of these parallel efforts, like ours, were being driven from the Defense community. So, this introduction begs a couple of questions:
- Why would someone want to create a Cyber Security Consortium?
- Why should something like that, if it were necessary, tend to be spear-headed by Defense contractors?
- What does all of this have to do with innovation and technology?
In response to the first question - the reason why Cyber Consortia are necessary is due to the complexity of the problem space. When I began on the project, I had not yet run across any organization that had developed a comprehensive Cyber Security methodology and the notion of a single solution to cover all aspects of security has been a non-starter for a long time. In fact, there were very few organizations that were even tracking or managing security architecture at that point. While there has been some improvement in these areas over the past 3 or 4 years, it is still relatively uncommon to see these things being practiced in larger enterprises.
When we're referring to complexity here what we really mean is the extraordinary stack of tools, processes and knowledge that is required for anyone to fully understand let alone counter-act a juggernaut of disruptive technology designed primarily to defeat standard enterprise security paradigms. There are literally dozens of areas of specialization now in this field and only a handful of organizations on the planet have the resources to evaluate and experiment with most of them. And even those few organizations that can tend to be forced more or less to play catch-up as new developments emerge.
What was needed was not one organization to track and react to the full scope of Cyber Security evolution, but rather a community approach. The community approach for managing Cyber exploits began in the late 1990's - this provided an elementary model for much more complex collaboration approach.
In response to the second question - The defense community in reality serves both government and commercial clients (something called the Defense Industrial Base or DIB). Companies like Lockheed Martin, SRA, Serco and Northrop Grumman (and many other systems integrators) all tend to have both the resources and relationships necesasary to help make something like a Cyber Consortium happen. Also, in the past several years as the Federal government moved from an IA perspective to Cyber Commands, for the first time companies were being asked to support requirements for comprehensive management of Cyber Security issues - defense contractors were thus the first to respond to such needs.
In response to the third question - It turns out that this problem space represents an ideal case study into how super-complex problems can be dealt with across dozens of entities to help redefine both technology and practice across an entire industry. No one company or organization was capable of fully managing the problem space on its own - however, through the consortium construct many specific individual issues could be tackled within a shared solutions methodology and practice framework.
 |
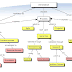
| This is a prototypical Consortium framework |
In part 2, I will explore the components of a Cyber Consortium (depicted above) and in part 3 I will illustrate how this approach is applied to specific aspects of Cyber Security technology and utilized to resolve security challenges.
Copyright 2012 - Technovation Talks, Semantech Inc.













0 comments:
Post a Comment