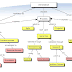
- Doctrinal Concept 1 – Cyberspace is an active battlespace; in other words Cyberwar is today’s new proxy battlefield, it is the new “cold war.”
- Doctrinal Concept 2 – Cyberspace is not just about defense; in fact, the view of the NETOPs environment as a reactionary architecture is one of the reasons it cannot keep pace with emerging threats. Offense is needed.
- Doctrinal Concept 3 – Cyberspace is a rapidly changing paradigm, the current processes for deploying capability are not yet aligned to this rapid pace.
- Doctrinal Concept 4 – Cyberspace combines systems (information & weapons systems) and communications in ways previously not imagined. This has a strangely unifying effect, eventually merging the systems involved. Some of this is intentional, some of it is an accidental byproduct.
- Doctrinal Concept 5 – Cyberspace is not and cannot easily be segmented, the overlap across various participants complicates action and mission success. Coordinated missions will become the norm.
- Doctrinal Concept 6 – Cyber “events” occur within a context – in fact they form patterns which can be modeled, predicted and mitigated.
- Doctrinal Concept 7 – Cyberspace represents a previously unavailable route of access to government (or any confidential) information and capability; however the approach towards security and privacy must still be balanced against common sense and the core principles upon which the nation was founded.
- Doctrinal Concept 8 – The most important “Cyber-weapon” is and always will be the human mind; management of Cyber Operations must foster innovative and agile decision making. Threats must be addressed proactively and with a minimum of bureaucracy in order to match the natural advantages held by potential Cyber opponents.
 |
| Cyber Attacks are not random events... |
Copyright 2012 - Technovation Talks, Semantech Inc.













0 comments:
Post a Comment