The Obama administration announced yesterday that sanctions were being placed on Russia in retaliation for the 2016 Election Hacking scandal. Shortly after that announcement, a Joint Analysis Report (JAR) was released providing a description of the nature of the Cyber attacks. It's still not clear if this report (released to scribd.com) is the complete intelligence report that the President had requested some weeks back or one perhaps one of several. What is clear however, is that the level of detail is perhaps more granular than expected, but the scope seems to be narrower than it could have been.
 |
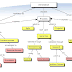
| Architectural representation of the Election Hacks from FBI Report: JAR-16-20296 |
So what did we learn from the document? Here are a few highlights:
- We have a relatively straightforward diagrammatic view of how the attacks occurred (I've placed an example of this in the post image)
- We've been given a glimpse into the nature of the Russian Intelligence Service (RIS), but a limited one. Approximately two dozen names are listed as being associated with the RIS, but it's not clear if all these are indeed separate groups (and no explanation is given about any of it). There are some very Bond-like spynames in the group like CrouchingYeti, Fancy Bear and Gray Cloud but that in itself isn't very illuminating.
- We are shown some detail regarding the identity of the exploit. Unfortunately, this is not provided in a context that might be well-understood outside of the Intelligence Community or a small cadre of Cyber security experts. The exploit information is supposed to clinch the identification of the groups in question and maybe it does, however it certainly seems as though part of the story is missing.
- Fully half of the document is dedicated to describing various Cyber risk factors and mitigating actions in some detail. While this is good information, it is terribly generic and it seems a though it has been used to inflate the size of the report somewhat - perhaps at the expense of the main point for releasing it.
While I don't wish too sound too critical here, I think it might be worthwhile for the folks working on this analysis to consider creating another draft. First, I'd like to address why I think that's necessary and then I'll delve into what ought to be revised or added in the next version of the report.
The reason why we need to get this right should be obvious, but I'll state it again anyway. The report represents the foundation for both the claims that the attack occurred as well as for the sanctions that will follow. This may or may not represent a form of Cyber-warfare (both the attack and the response - I've outlined that topic in more depth here). In any case, it is a serious matter and the sanctions probably represent the most severe actions we've taken against Russia since the end of the Cold War. Thus the foundation needs to be as a strong as possible. Obviously, there are national security issues at play with this topic, however in some situations, more information can be better than less. The information missing from the current version of the report includes the following:
- Detail on the other organizations which were hit in the attack - there is an implication of a much wider attack, but no specifics.
- An explanation of the context - the goals of the attack and how the stolen information was utilized. Also, there needs to be an explanation of the process of exploit identification for those who aren't already familiar with it.
- A discussion of how the US can help safeguard election processes and systems. This is somewhat covered by the best practice portion of the report, but that seems to also be saying that all such mitigation for thwarting future attacks is entirely up to each potential target which isn't altogether satisfying. We should be having stronger a dialog on how critical processes can be protected by the groups we thought we there to perform that task. For example, who if anyone, will take the lead on auditing voting systems in every state?
The current Grizzly Steppe report seems to have give us the bare minimum. We need more than that if we wish to learn from this experience and keep it from happening again. Let's give it another try...
copyright 2016, Stephen Lahanas













0 comments:
Post a Comment